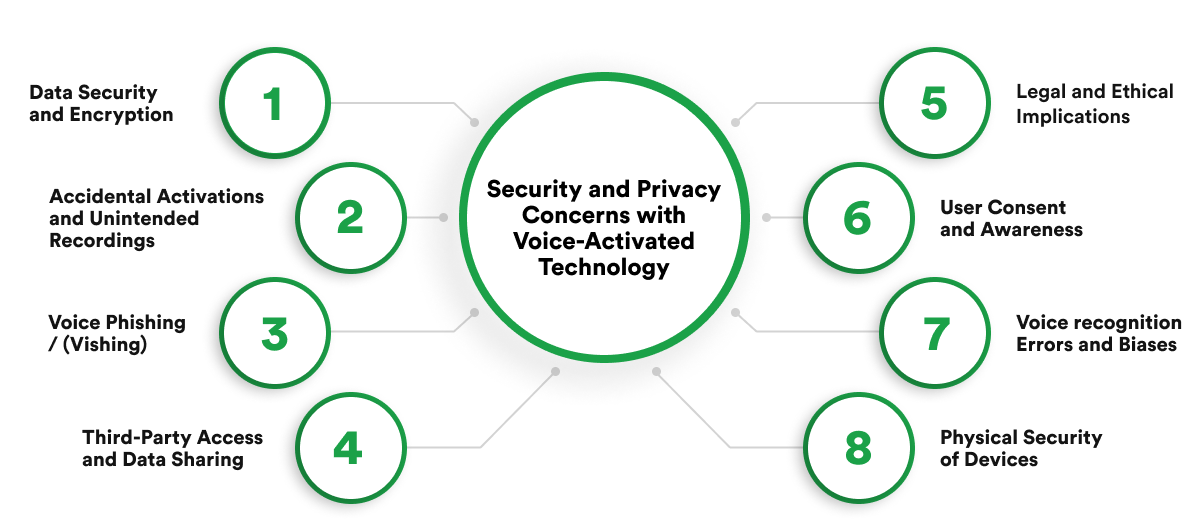
Voice recognition systems collect, store, and process extensive voice data, ranging from raw recordings and transcripts to metadata about speech patterns and usage contexts. This data is typically sent to cloud servers or stored on local devices, where it is used to train and refine AI algorithms for improved accuracy. However, this process exposes sensitive information to several risks, including data breaches, unauthorized access, and misuse of personal data.
The aggregation of voice data across multiple industries increases the potential attack surface for cybercriminals, who may target this information to launch identity theft or fraud. Implementing rigorous encryption protocols and strict access controls throughout the data lifecycle is essential to control these risks.
Key Vulnerabilities in Voice Systems
1. Voice Spoofing and Cloning
Voice spoofing and cloning are among the most pressing threats to voice recognition systems. Attackers can use advanced techniques, from replay attacks to sophisticated deepfake technology, to replicate an individual’s unique vocal characteristics. Cybercriminals can bypass biometric authentication measures by generating synthetic voices that closely mimic legitimate users’ speech patterns.
For instance, in automotive, attackers could spoof a driver’s voice to trigger unauthorized commands or intercept communication between the vehicle and its cloud-based services. The interconnected nature of modern vehicles, often part of larger IoT ecosystems, further amplifies the risk of unauthorized access and data breaches. Robust anti-spoofing algorithms and continuous monitoring are essential to detect subtle discrepancies between genuine and manipulated voice inputs.
2. Unauthorized Device Access
Another major vulnerability is unauthorized device access. As voice recognition systems are increasingly integrated into a wide range of connected devices, from smartphones and smart speakers to automotive infotainment systems, these endpoints become attractive targets for attackers. If these devices are not appropriately secured, malicious actors can exploit weak default settings, outdated firmware, or unprotected APIs to gain entry. Once inside, attackers can manipulate commands, access stored voice data, or use the device as a pivot point to infiltrate a broader network.
3. Interception and Eavesdropping
Interception and eavesdropping pose significant risks, mainly when voice data is sent over unsecured or poorly encrypted networks. Cybercriminals can exploit vulnerabilities in wireless communications to capture voice commands as they travel between the device and cloud servers or other endpoints. This intercepted data may include sensitive personal information, command instructions, or even biometric voiceprints, which can be used for further fraudulent activities.
For instance, in healthcare, unauthorized access to voice recordings or transcripts could expose confidential patient details, potentially violating regulations such as HIPAA. To counter these threats, end-to-end encryption protocols and secure transmission channels are critical to ensuring that intercepted data remains unintelligible to unauthorized parties.
4. Replay Attacks
Replay attacks involve capturing a legitimate voice command and reusing the recorded audio to gain unauthorized access. In such attacks, an adversary records a user’s voice during a valid authentication process and later plays it back to the system. It may accept the replayed audio as genuine if the system lacks robust countermeasures, such as time-stamped tokens or challenge-response mechanisms. This type of vulnerability highlights the importance of incorporating dynamic authentication techniques that detect and reject repeated or out-of-sequence voice commands.
5. Injection Attacks
Injection attacks in voice recognition systems refer to inserting malicious or unauthorized audio signals into the communication stream. Cybercriminals may use these tactics to embed inaudible commands or alter the expected command structure, tricking the system into executing unintended actions. These attacks can compromise the system’s integrity, potentially leading to unauthorized transactions or system control.