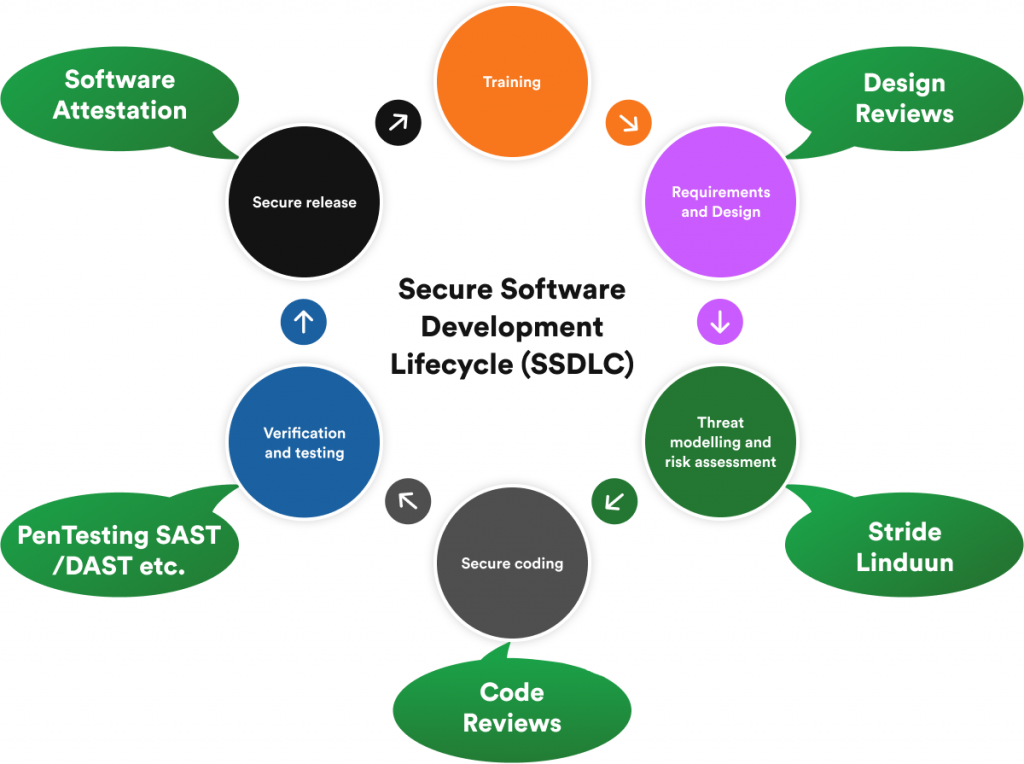
3. Threat Modeling and Risk Assessment
Threat modeling risk assessments help development teams identify potential vulnerabilities using a real-world attacker mentality. Simulating possible attack scenarios and implementing countermeasures to the software design will go a long way to mitigate risk and ensure security, privacy, and compliance.
This approach also helps organizations develop robust incident response plans. Examining code from all angles using a comprehensive review or analysis process also helps keep your application compliant and secure after release.
This is also an excellent time to set secure defaults to closely align with other platform security features. This is much easier than educating various administrators later.
4. Secure Coding
Secure software development depends on established secure coding guidelines and standards. Experts who take industry best practices into account must define these secure coding guidelines and measures.
Secure coding guidelines will also encourage the creation of improved design principles that will minimize potential vulnerabilities when the software goes live. Establishing a standard set of rules will also dictate what kind of code programmers will write and the enforcement of reliable testing methods throughout the SLDC.
5. Verification and Validation
During the SLDC, it will help to leverage the V-Model that promotes the execution of processes in a sequential (V-shaped) manner.
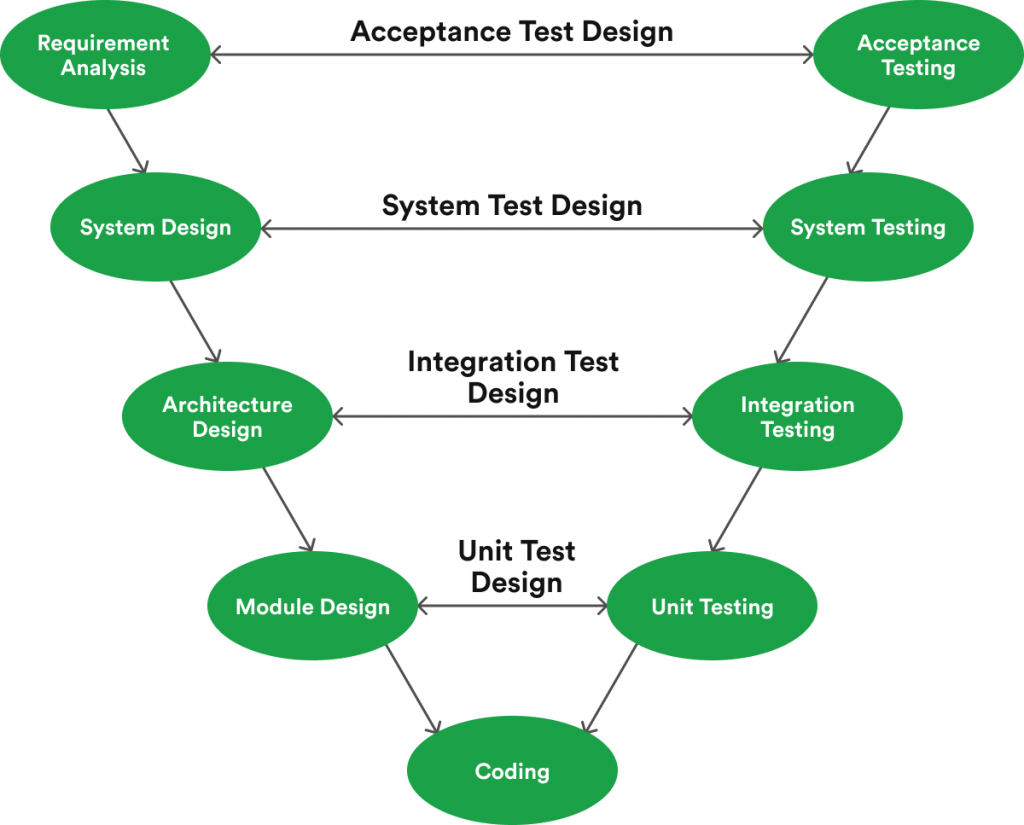
This approach, an extension of the waterfall model, ensures that testing occurs during each corresponding development stage. In this scenario, each step in the SLDC directly relates to a testing phase.
6. Secure Release
When software products go live, several instances will be running in concert across different environments. Before long, you will find that some users will update to new versions and patch their software while others won’t.
As such, organizations must implement environment management protocols, real-time monitoring, incident response plans, and ongoing security checks. This approach will help fortify your software after release.
At this juncture, it’s also important to engage in penetration testing. In this case, the best way forward is to hire an ethical hacking team to identify potential risks missed by in-house security teams.
These white hat security experts leverage the tools and tactics used by hackers to evaluate your security posture. Most often, it’s best for companies to engage in some form of penetration testing every month to stay a step ahead of bad actors.
Doing all this throughout the SLDC helps developers understand and remain alert to common vulnerabilities. By avoiding repeat occurrences, software engineers can enhance the SDLC.