
AI-Powered LiDAR: A New Era of Perception
How AI and ML enhance LiDAR technology by overcoming data processing challenges, enabling advanced applications in autonomous systems, robotics, and 3D mapping, and more.
rinf.tech Automotive Cybersecurity Study

Software Architect at rinf.tech
As cybersecurity threats increase rapidly, the Automotive industry is among the key targets of cyber attacks.
Modern cars’ evolution is driven by autonomous driving, electrification, and connectivity. The more automated and data-laden the vehicle, the higher the risk of cyber attacks and challenges.
To better understand how Automotive software development companies and other industry actors should mitigate functional safety and cybersecurity risks during their solutions development, testing, and deployment, we at rinf.tech have conducted our Automotive Cybersecurity study.
To explore the current trends and the future path of cybersecurity evolution in Automotive, we have analyzed available research platforms such as Web of Science, IEEE Xplore, etc., as well as relevant Think Tank publications, and other sources.
In addition, we’ve scrutinized the existing landscape of Automotive Cybersecurity standardization and regulations to better understand who sets the demands and how they should be met.
In this article, we would like to share our Automotive Cybersecurity study findings and conclusions that might be of interest to the global Automotive software engineering and business communities.
According to the Oxford dictionary, “cybersecurity” means “the state of being protected against the criminal or unauthorized use of electronic data, or the measure taken to achieve this.”
This criminal or unauthorized usage is quite vast. It includes invading privacy and stealing properties like money from a financial system or goods of any kind by gaining access to offices, warehouses, and even homes.
With the latest growth of connectivity in the Automotive domain, the vulnerabilities grow as well. Still, one fundamental aspect must remain in focus: Functional Safety (ISO 26262). As such, every automotive software engineer must consider different scenarios that can threaten the safety of car drivers and their passengers by exploiting vulnerabilities either by direct intention or implicit consequence of their actions.
According to management consultancy McKinsey & Company, modern cars feature around 100 million lines of code, which is expected to triple by 2030. In comparison, a passenger aircraft contains about 15 million lines of code, and a PC OS has up to 40 million lines of code. Increasing complexity increases the chances of cyber-attacks [1].
Considering the recently reported attacks on vehicle networks, it has become clear that cryptography is vital for assuring the security of in-vehicle and inter-vehicle communications.
Solving such problems requires a high degree of knowledge sharing in the industry, particularly between car manufacturers and their supply networks. One organization that does that in the United States is the Automotive Information Sharing and Analysis Center (Auto-ISAC). Industry members share and analyze information about any possible risks to vehicles, thus strengthening cybersecurity technologies. But a worldwide holistic approach is also needed [1].
United Nations Economic Commission for Europe (UNECE) is one of the five regional commissions under the jurisdiction of the United Nations Economic and Social Council. It was established to promote economic cooperation and integrations among its member states.
From the beginning, addressing cybersecurity issues in modern cars was a matter of good practices and did not represent a formal regulatory requirement to claim for vehicle type approval. This aspect changed after UNECE WP.29 regulation R155 for CSMS (Cyber Security Management System) was adopted by UNECE’s World Forum for Harmonization of Vehicle Regulations.[2]
In the context of UNECE WP.29 regulations, two new documents have recently been emerged, covering key future topics:
I. Cybersecurity (R155) that is the focus of this article [2], and
II. Software Update (R156) that extends the context in the future [3].
New requirements for cybersecurity can be segmented into two main categories as follow:
a. Establishment of a Cyber Security Management Systems (CSMS) covering organizations’ policies and processes for handling cyber risks related to the entire lifecycle of vehicles, equipment, and services.
b. Activities and documentation related to the secure development of automotive items and post-development activities such as production, operation, maintenance, and decommissioning.
These targets will have to be achieved and demonstrated by the OEMs and the rest of the automotive supply chain that should be authorized to push new vehicles to the market, according to the above-mentioned regulations.
As mentioned above, Functional Safety is of utmost importance for the entire supply chain in Automotive. There are already standards addressing it that are based on specific system information, such as ISO26262. However, it doesn’t cover risks created by outside world interference. This is exactly where cybersecurity becomes critical due to its system-extrinsic nature. Risk sources are numerous nowadays, and their potential impacts could also be extended further than just safety aspects.
Evaluating potential damage for automotive systems is based on three key pillars:
In the context of cybersecurity, the typical approach for impact rating is to evaluate it against four dimensions (aka SFOP):
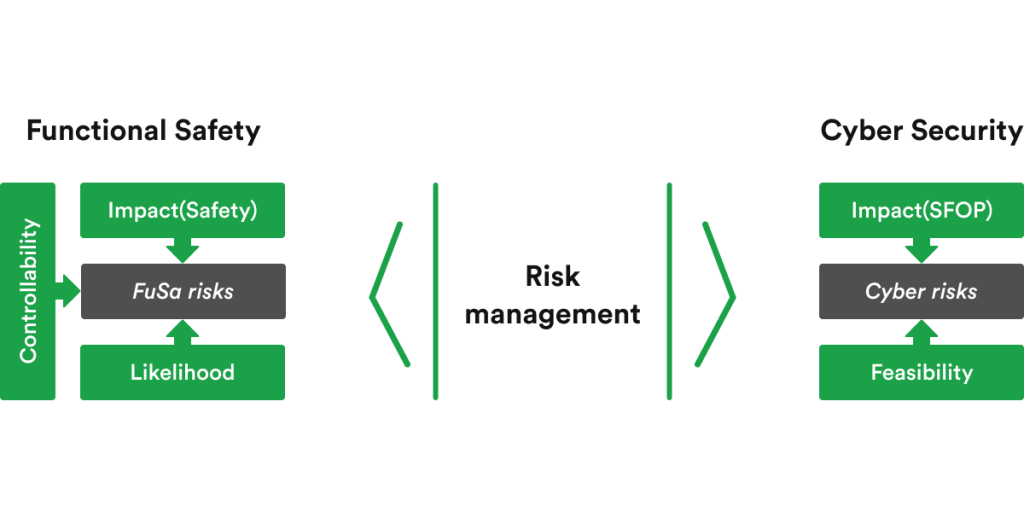
To implement these approaches and new processes, a new standard called ISO/SAE 21434 has been published (last release: FDIS: March 2021) for defining the framework that organizations must put in place to better handle cybersecurity, in alignment with other relevant references such as ISO26262.
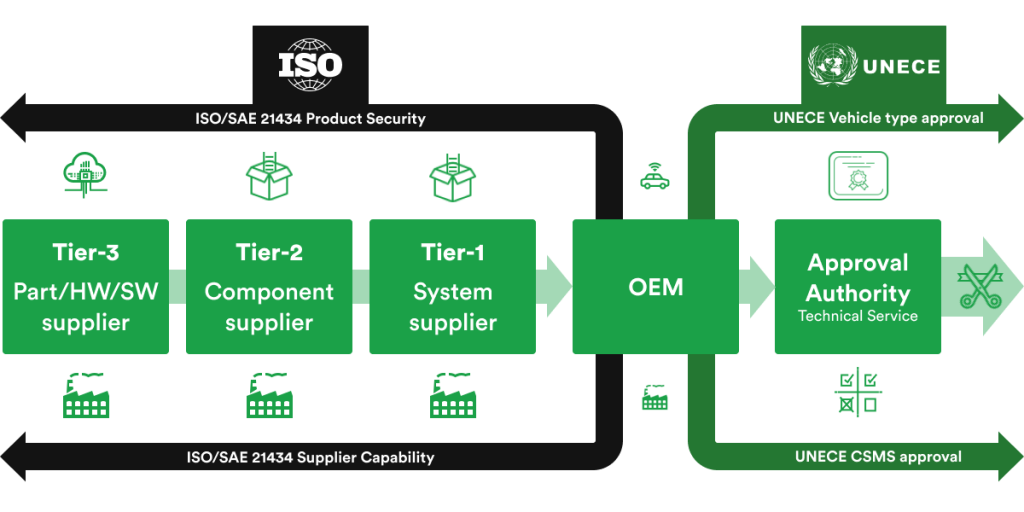
ISO/SAE21434 requires a security and response management and is divided in the following clauses:
Clause 5. Organizational Cybersecurity Management
From the Organizational perspective, to enable cybersecurity engineering, there is the need to institute, instill and maintain cybersecurity governance and cybersecurity culture, including awareness management, competence management and continuous improvement.
Clause 6. Project-Dependent Cybersecurity Management
It describes the requirements for cybersecurity development activities management for a specific project.
Clause 7. Distributed Cybersecurity Activities
Only applicable if responsibilities for cybersecurity activities for an item or component are distributed. This clause describes management of distributed cybersecurity activities and applies to:
Clause 8. Continual Cybersecurity Activities
Cybersecurity activities are not limited to only one part of the development process; they are performed during the entire lifecycle and can be done outside of a specific project:
Clause 9. Concept Phase
Vehicle level functionality, as implemented in items, should be well known, and considered in this clause. For this purpose, cybersecurity goals are specified, and cybersecurity risks are assessed by using methods specified in Clause 15. Furthermore, cybersecurity claims are formulated and used to explain why risk retention or sharing are considered adequate.
Clause 10 – 11. Product Development
It defines the cybersecurity specification including architectural design, implementation, verification of cybersecurity requirements and cybersecurity validation of an item at the vehicle level.
Clause 12 – 14. Post-Development Phase
It ensures that a product is compliant to cybersecurity-related aspects from the manufacturing and assembly perspective. Capabilities to react properly on occurred cybersecurity incidents is established including maintenance and updating of the items and components.
As a final aspect, requirements for decommissioning shall be considered, especially in the context of data protection.
Clause 15. Threat Analysis and Risk Assessment
Assessment methods include modular methods for analysis and assessment to determine the extent of cybersecurity risk in order for it to be mitigated/eliminated.
In the world of Automotive, standardization is the key.
As cybersecurity-related activities in the automotive industry evolved, so did the Automotive Open System Architecture (AUTOSAR), aiming to satisfy the most acute cybersecurity requirements. Secure Boot mechanism and Secure On-Board Communication mitigate the physical aspect of an attack. However, being permanently connected to the external networks through vehicle to cloud (V2X) or vehicle to vehicle (V2V) communication enables new attack channels that must be considered during automotive software development.
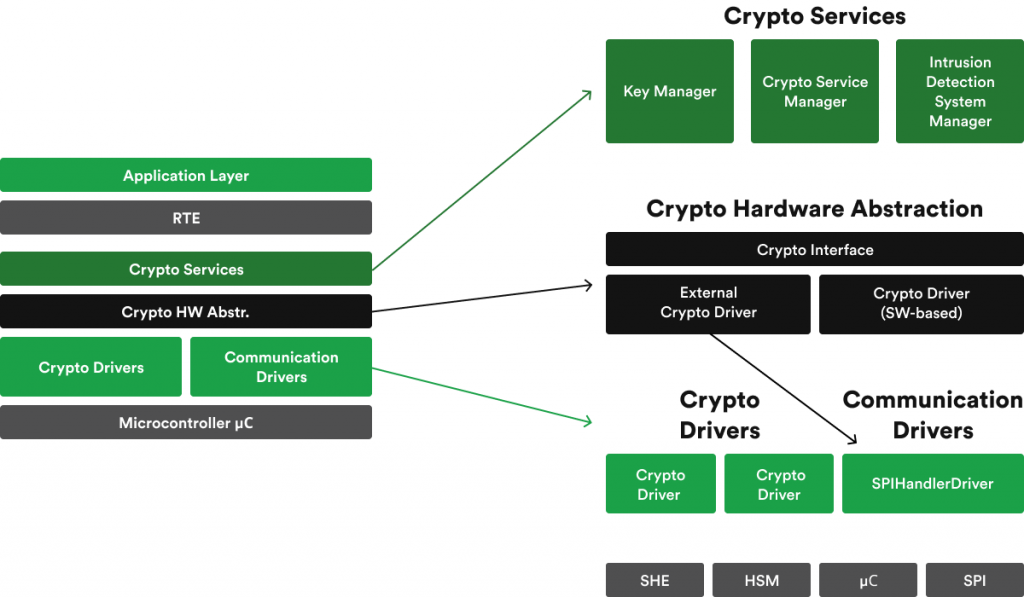
As a foundation for the new cybersecurity mechanisms, AUTOSAR uses already existing cryptography mechanisms grouped in what engineers typically call the Crypto stack of the AUTOSAR. The well-known crypto modules are divided between the abstraction layers to abstract from the location of cryptographic primitives realized by internal or external hardware accelerators or software-based implementation.
This is realized by the Electronic Control Unit Abstraction layer, providing similar mechanisms to access internal or external cryptographic devices or software implementation of the primitives.
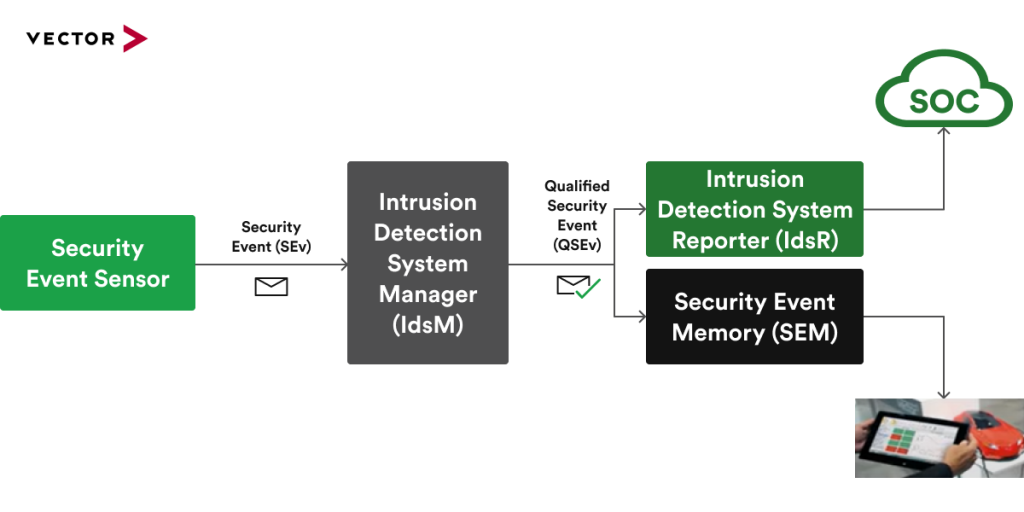
The Service layer, on the other hand, implements a new module called Intrusion Detection System Manager (IDSM) alongside the Crypto Service Manager that is responsible for the management of cryptographic jobs, and the Key Manager that interacts with the key provisioning master (either in NVM or Crypto Driver) and manages the storage and verification of certificate chains.
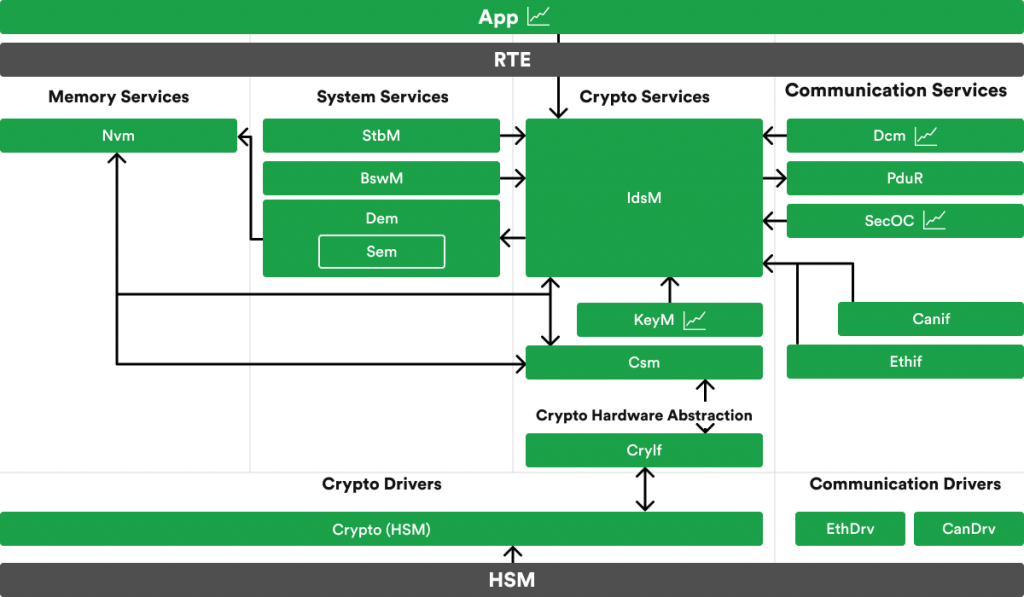
The root of IDSM is Security Events (SEv) which are useful for offboard forensic analysis. A sequence of security events reported from multiple vehicles should help to identify attack vectors. Each SEv has a unique security event ID to unambiguously identify the kind of security event. Security events can even be related to diverse assets like CAN/Ethernet communication, diagnostics, crypto material, changing communication, and others [5].
A SEv can be:
Besides collecting SEvs, the IDSM has the capabilities to qualify SEvs according to configured rules and create Qualified Security Events (QSEvs) that are further stored by IDSM or forwarded as useful data for the security forensic performed at the backend.
Vector is one of the leading AUTOSAR providers that has long proven its capabilities of providing state of the art solutions regarding market needs. Cybersecurity solutions offered by them are no different. In fact, their proactivity is one of the reasons why AUTOSAR includes an Intrusion Detection System (IDS) since Vector is the main initiator of standardizing this solution for the Automotive cybersecurity world.
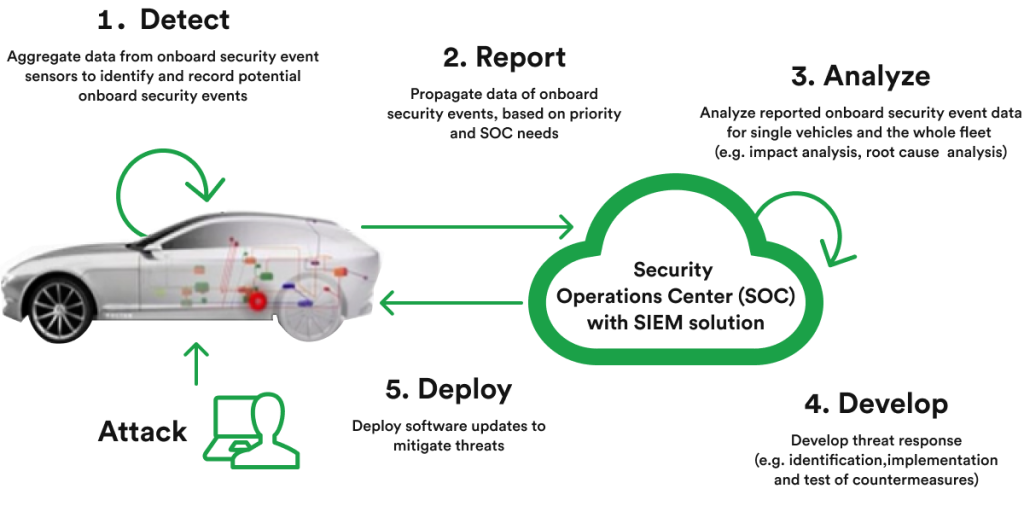
Vector offers fully configurable, out-of-context developed software to satisfy the latest AUTOSAR requirements and specification not only for IDSM but the entire Crypto Stack starting with drivers that operate Hardware Security Modules (HSM), on-chip or external, including software implementation of the cryptographic primitives for authentication, integrity check, key management, symmetric and asymmetric cryptography, and others. This aspect is important from the perspective of solution rate of maturity and robustness.
In the very near future, all OEMs will likely rely on Intrusion Detection Platforms according to the concept and design provided by Vector.
Over the past few years, Automotive cybersecurity research has gained much steam. It provides significant value for the ecosystem of Automotive technology developers. Academic community direction is one of the market predictors for the accommodation of new technologies. So is the case with an increasing interest in Automotive Cybersecurity within the academic domain in the past three years, as suggested by simply browsing platforms such as Web of Science [6], IEEE Xplore [7], and others.
The analysis of the available publications related to Automotive Cybersecurity draws the conclusion that the past three years have given start of a Gartner hype cycle:
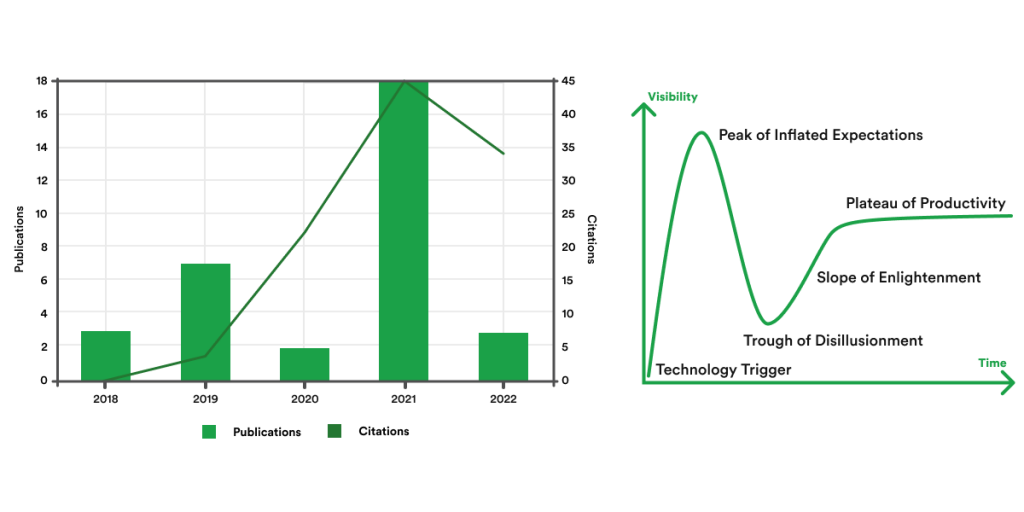
This might be a good indication that the maturity of the emerging technologies has not reached a settling phase yet, and there is still room for enlightenment and improvement regarding this topic.
Metrics related to the latest publications tell us that Automotive Cybersecurity research has attracted a multidisciplinary interest. It’s interesting to note that relevant studies have been conducted by not only Computer Science Universities but also by Transportation Science and Technology, Telecommunications, and even Law, Criminology and Penology Universities:
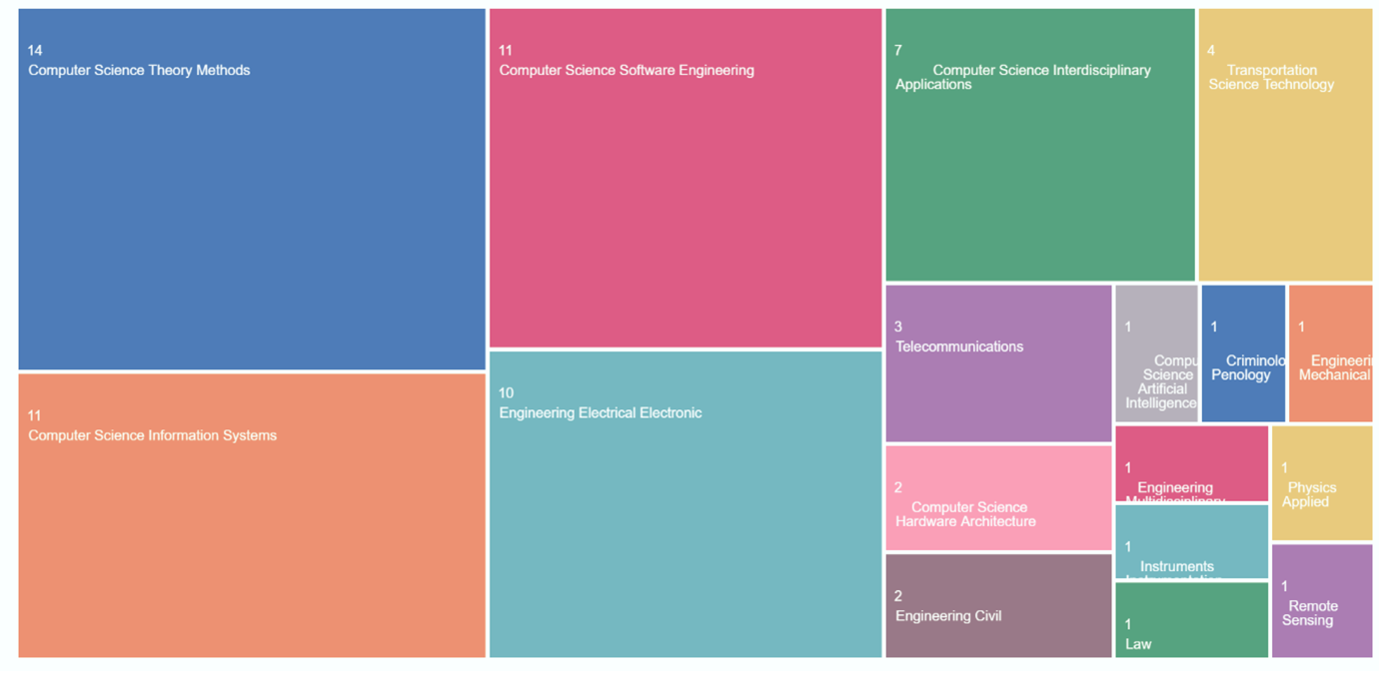
Knowing all this information leads to another question: what are the key study topics?
While, initially, engineers would think more of a physical approach to a cyberattack, as seen in Figure 9, the latest publications demonstrate that the focus has shifted to more up-to-date terms, as seen in Figure 10.
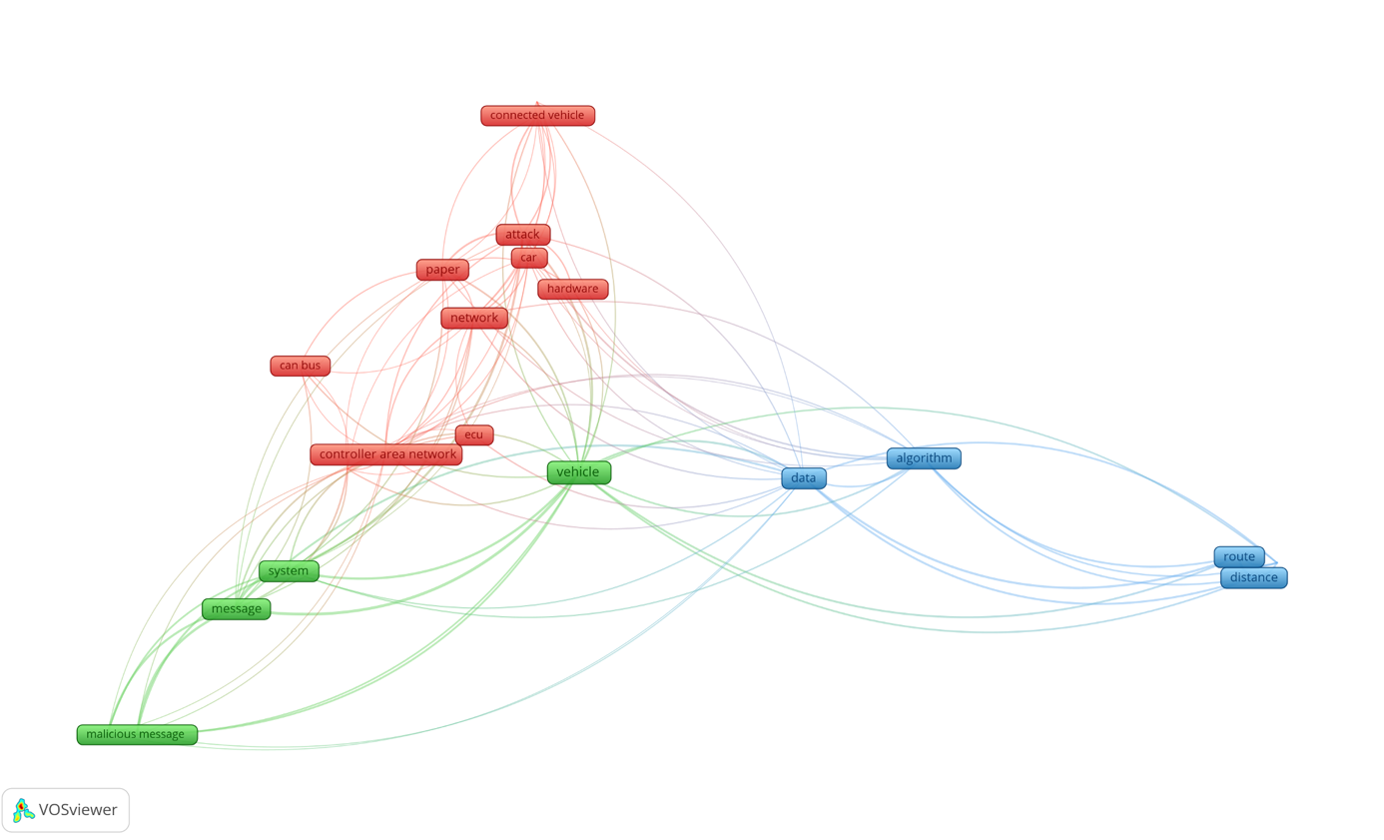
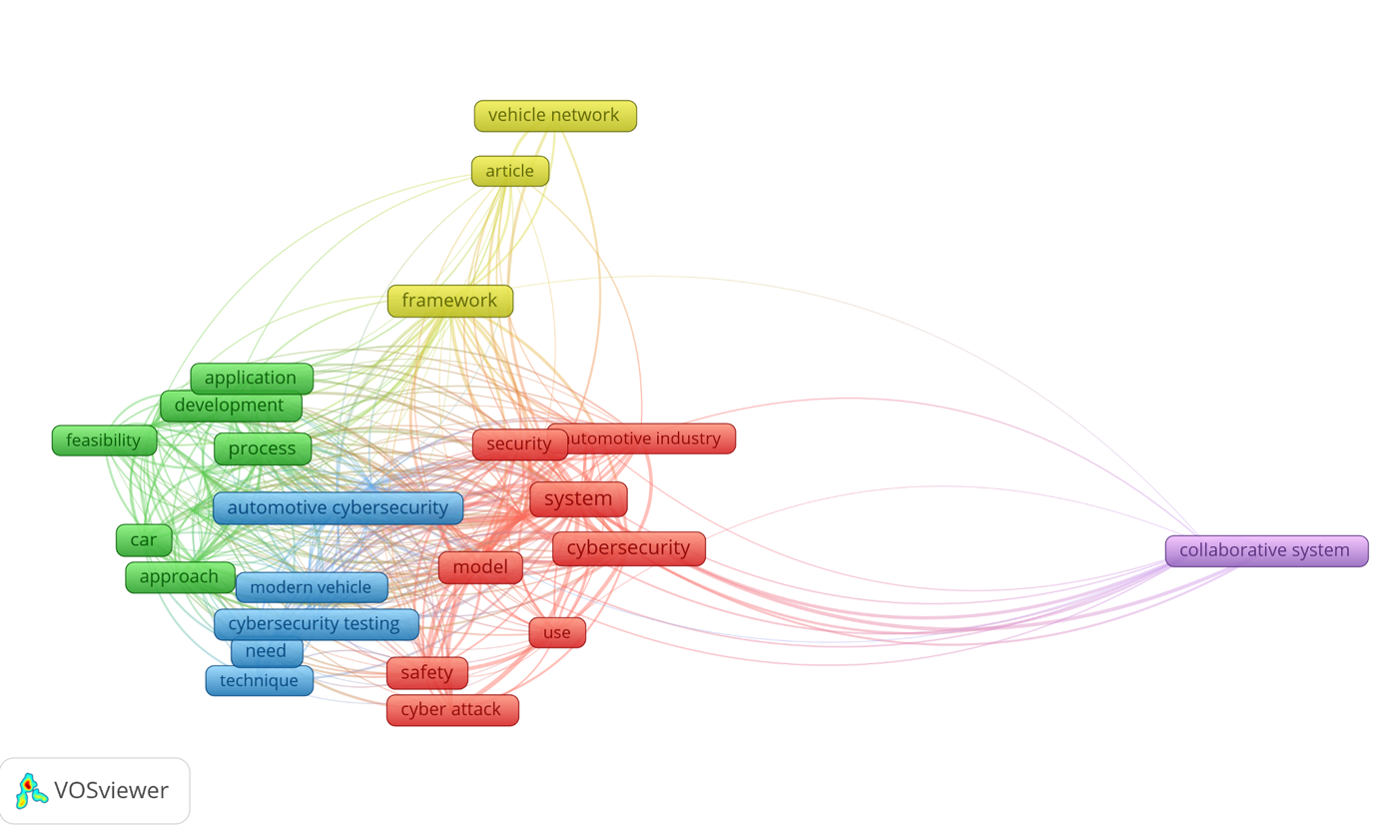
The Safety aspect is still and will always be in focus. However, terms like “collaborative system”, “cybersecurity testing”, “vehicle network” are keywords to predict a direction of expansion for Automotive Cybersecurity. Even though they are addressed in Computer Science or other studies and are present on the market in different domains for quite a while, it looks like the Automotive industry is finally ready to welcome this mechanism and tailor it to its specific needs.
We can observe that standardization is another topic also presented in Figure 10, highlighted by terms like “iso sae”, “process”, “risk assessment”, and others associated with the cluster drawn in green, confirming that ISO/SAE 21434 is long awaited by both academia and market.
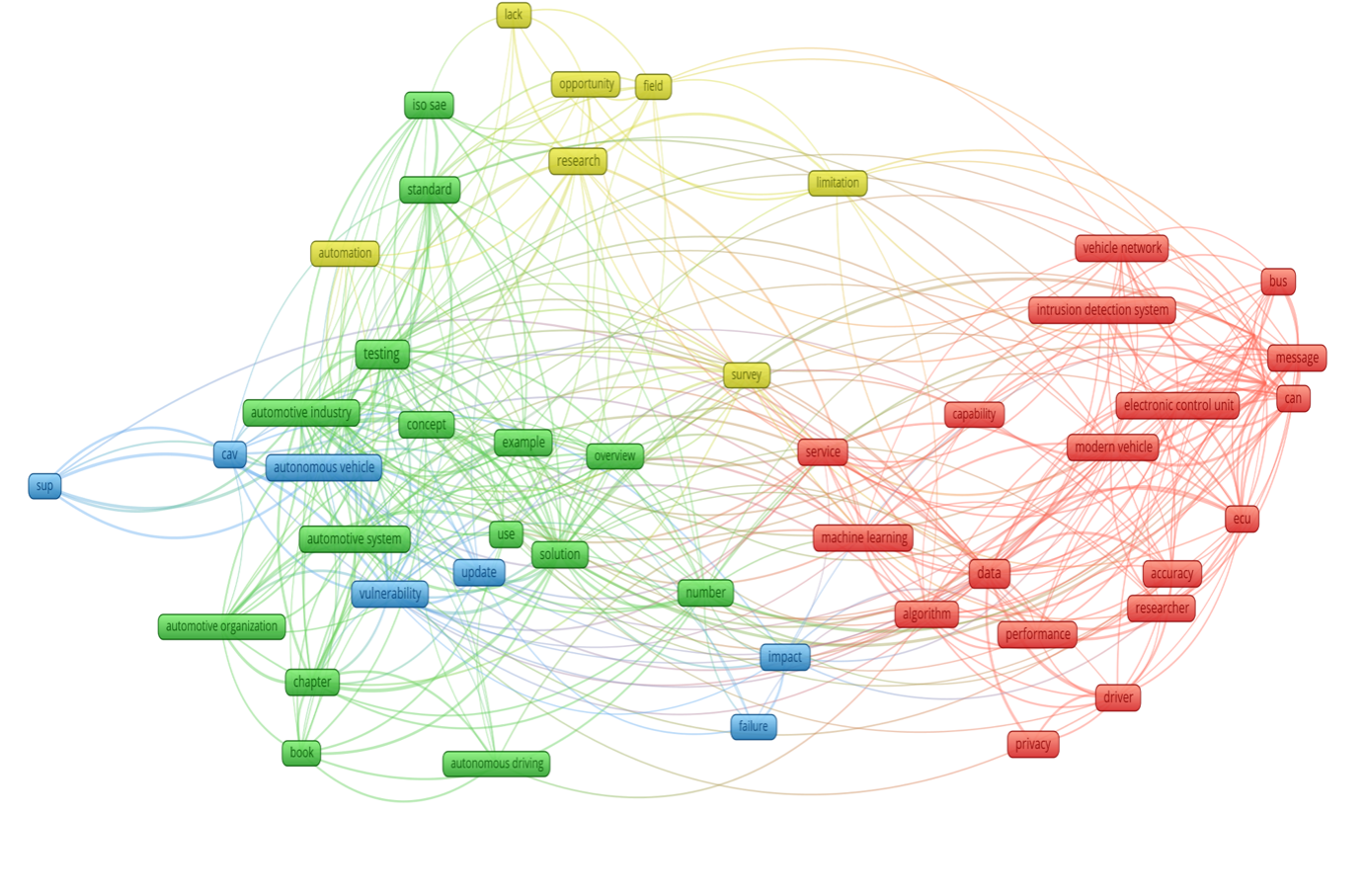
Suppose we also include a related Scientific Newsletter in our compilation. In that case, a bigger picture comes up – an image of ongoing activities already existing on the market like the above-mentioned “Intrusion Detection System” that has been defined and provided by Vector to satisfy the “Collaborative Systems” already identified in Figure 10.
In Figure 11, we can see the term “limitations,” which is better aligned with the real world that the Automotive market relies on so much. It is tightly connected in the red cluster to terms of physical nature like “bus”, “can”, “message”, as well as to “algorithm” and “data” involving the software limitation aspects.
These aspects are often related to the computing performance limitations imposed by a classical Automotive dedicated processing power – a tradeoff often made to save costs. This is one of the reasons why High Computing Platforms (HCP) based vehicle architecture has been gaining traction and why we can now discuss an improvement that opens the door to more complex software to be built.
More complex algorithms can now satisfy the needs of Cybersecurity and other aspects of modern vehicles. According to EY, to achieve this, Automotive companies should avoid silos and focus on building an ecosystem of reliable long-term technology partnerships with providers that have deep domain knowledge and proven solutions delivery capabilities.
To build cybersecurity solutions that can effectively address the current and future threats and risks, car makers should gain quick access to critical technologies and capabilities.
Technological disruption is rapidly turning the traditional car into a “computer on the wheels.” The three main driving forces – autonomous driving, electrification, and connectivity – do not only impact new transportation models and growth opportunities, but also give rise to several complex functions that will soon become the mainstay of auto products.
Companies operating in the automotive industry are affected by the increasing complexity of research and development, the shift from hardware to software, and shorter product life cycles. They also have to coexist and compete with a highly dense startups ecosystem. As the technological breakthrough reshapes the automotive industry, EY analysis shows that automotive executives are increasingly looking at strategic partnerships (rather than outright acquisitions) with technology companies as the way forward for faster access to capabilities, technologies, and products.
As such, partnerships with technology firms are the optimal strategy for supporting cybersecurity product integration agenda and enhancing the customer experience throughout the product life cycle.
[1] “ISO – CYBERSECURITY IN THE DRIVER’S SEAT,” https://www.iso.org/news/ref2584.html
https://www.iso.org/news/ref2584.html (accessed Sep. 05, 2022).
[2] “UN Regulation No. 155 – Cyber security and cyber security management system.” https://unece.org/transport/documents/2021/03/standards/un-regulation-no-155-cyber-security-and-cyber-security (accessed Sep. 05, 2022).
[3] “ISO/DIS 24089 Road vehicles — Software update engineering.” https://www.iso.org/standard/77796.html (accessed Sep. 05, 2022).
[4] “CertX,” UNECE WP.29 / R155 – How Cyber Security will impact the automotive market as of June 2022, 2022. https://certx.com/automotive/unece-wp-29-r155-how-cyber-security-will-impact-the-automotiva-market-as-of-june-2022/ (accessed Sep. 05, 2022).
[5] “Intrusion Detection System Manager.” https://www.autosar.org/fileadmin/user_upload/standards/classic/21-11/AUTOSAR_SWS_IntrusionDetectionSystemManager.pdf (accessed Sep. 13, 2022).

How AI and ML enhance LiDAR technology by overcoming data processing challenges, enabling advanced applications in autonomous systems, robotics, and 3D mapping, and more.

Offering insights into how the latest AI advancements will impact consumers, manufacturers, and the broader environment in 2025 and beyond.

Showcasing the environmental and economic benefits of integrating sustainable materials and robust recycling practices into the automotive value chain.